Stablecoins have started to win remittances and cross-border payments, but now they need to win the boardroom.
Startups use them. Freelancers rely on them. But the world’s largest corporations are still watching from the sidelines. Why?
Because for the boardroom, it’s not just about speed and cost. It’s about control, discretion, and regulatory clarity.
In this post, we explore what’s really holding enterprise adoption back and how zero-knowledge proofs and MPC could unlock the next phase of stablecoin growth.
What would it take for large corporations to adopt stablecoins?
Stablecoins are already powering global payments. From remittances in Latin America to merchant settlements in Africa and Asia, they’ve become the de facto rails for fast, low-cost value transfer. But there's a glaring absence at the table: large corporations like Apple, Google, Facebook, and Amazon.
Imagine this: Apple using stablecoins to pay a key supplier in Shenzhen. On a public blockchain, that transaction could immediately reveal the supplier’s address, the amount transferred, and the timing, potentially exposing confidential supply chain relationships to competitors, traders, or even bad actors. A simple payment could unravel years of procurement strategy.
Take another example: Google disbursing stablecoin-based grants to AI research labs. On the surface, it sounds efficient. But now anyone can trace which labs received funding, how much they got, and when, long before Google is ready to make those investments public. For a company that thrives on strategic secrecy, this would be a nonstarter.
They’re not blind to the benefits. The allure of instant settlement, 24/7 availability, and reduced fees is undeniable. Yet adoption remains cautious, even conservative. So what’s holding them back?
Privacy.
Not secrecy. Not evasion. Butenterprise-grade privacy, the kind that gives corporations the confidence to operate at scale while meeting regulatory and strategic requirements.
What Do Large Enterprises Really Care About?

To understand their hesitation, we need to understand how large organizations actually operate. These aren’t scrappy startups chasing MVPs, they’re global institutions with layered decision-making, strict internal controls, and highly sensitive business relationships.
Every transaction may represent a strategic partnership, a confidential procurement agreement, or internal capital movement between entities. On a public ledger, that kind of visibility isn’t just uncomfortable, it’s a liability.
What large enterprises care about is:
- Discretion in payments – They don’t want suppliers, competitors, or even employees reading their financial activity on a block explorer. A payment to a new supplier, R&D partner, or regional entity could reveal sensitive business decisions.
- Regulatory alignment – These organizations aren’t looking to hide transactions; they just need to control who can see them, when, and under what legal basis. This is especially important when operating across multiple jurisdictions.
- Auditability – Internal finance, risk, and compliance teams need full traceability and audit logs, just not ones that are exposed to the public or competitors in real-time.
These aren’t theoretical concerns. For large enterprises, these are structural requirements, and they’re the reason stablecoin adoption stalls at the enterprise level despite its efficiency.
Tornado Cash and the Case for Controlled Privacy

For anyone unfamiliar, Tornado Cash was a smart contract-based protocol on Ethereum that allowed users to send and receive assets anonymously by "mixing" funds, effectively breaking the traceability of transactions onchain.
At its peak, it became a go-to tool for anyone seeking financial privacy on Ethereum, including individuals who simply didn’t want their transactions publicly visible. But it also attracted bad actors, including hackers and sanctioned entities, who used it to launder stolen crypto. This ultimately led to the protocol being sanctioned by the U.S. Treasury in 2022, and some of its developers were arrested.
This moment sparked a broader debate:
- Is financial privacy on blockchains inherently dangerous?
- Can anonymity exist without enabling abuse?
- And what responsibility do developers and infrastructure providers have?
The rise and fall of Tornado Cash taught us that the need for privacy on public blockchains is undeniable, but the path forward can’t ignore compliance. What institutions need isn’t secrecy — it’s selective visibility: the ability to preserve operational discretion while still meeting regulatory standards.
Secrecy, especially in fully open systems, tends to attract misuse. However, lack of privacy creates its own problems, from corporate espionage to regulatory risk. The key isn’t to eliminate privacy, but to build it with access controls, auditability, and accountability by design.
This is where we shift from the idea of “anonymity for all” to regulated, cryptographically-enforced discretion— the kind large institutions can actually use.
Privacy Without Secrecy: The Role of Zero-Knowledge Proofs

Zero-Knowledge Proofs (ZKPs) are a powerful cryptographic technique that allows someone to prove a statement is true without revealing the actual details behind that statement.
If that sounds abstract, here’s a real-world example you might already know: payment tokenization.
When you use Apple Pay at a store, the merchant doesn’t get your real card number. Instead, a temporary “token” is sent to process the payment. The payment still goes through, it’s still secure, and the bank can verify it, but your sensitive card details remain private.
ZKPs do something similar, but they work on a much deeper level, especially in the world of blockchain. They allow blockchain networks to verify that a transaction is valid without seeing all the sensitive details inside that transaction.
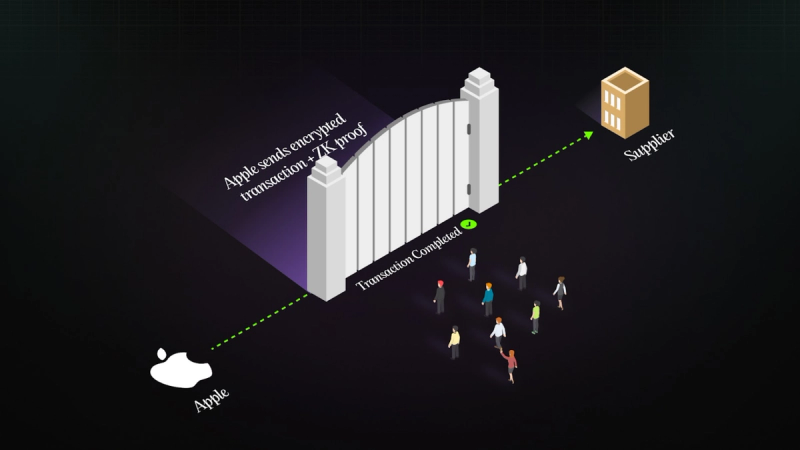
Apple and the Supplier: A Practical Example
Let’s say Apple is paying one of its manufacturing partners using stablecoins on a public blockchain.
Apple wants:
- The transaction to go through instantly
- Settlement to happen securely
- The blockchain to verify and record it
But Apple doesn’t want:
- The public to know who their supplier is
- How much they’re paying
- What the payment is for
This is where ZKPs come in.
With a ZKP-based system, Apple can encrypt all of that information (supplier, amount, reason) and generate a cryptographic proof that confirms:
- The payment was made to a valid business partner
- It complies with KYC/AML rules
- No funds were double-spent
- It stayed within preset transaction limits
The blockchain can then accept and record this proof, confirming that everything checks out, without exposing any of the actual data.
This is the essence of ZKPs: they separate proof from disclosure.
Breaking It Down
1. Shielded Transactions with Embedded Proof
At the transaction level:
- Apple’s payment data — amount, recipient, and purpose is fully encrypted.
- A ZK proof is generated showing the transaction is valid and compliant.
- That proof is submitted and recorded onchain.
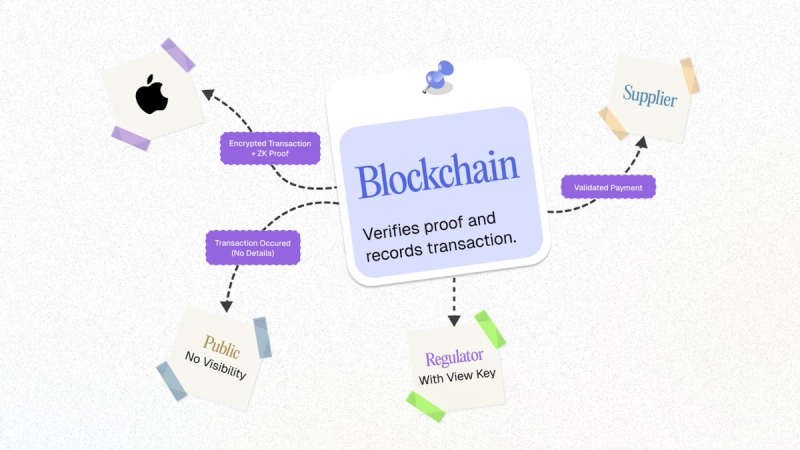
The result: The transaction is confirmed and processed, but no one on the public blockchain can see the details unless they have specific viewing rights.
2. Regulator View with ZK Access Grants
Now, let’s say Apple wants a regulator or external auditor to have visibility.
With ZKPs, Apple can provide view keys — cryptographic credentials that allow certain people to decrypt or view specific parts of the transaction.
For example:
- A regulator might be able to see the transaction amount and recipient, but not the purpose.
- An internal finance team might see the full data.
- Everyone else sees only the fact that a transaction occurred, with no details exposed.
This creates tiered access:
- The public gets zero details.
- Approved stakeholders get just enough.
- Apple stays in control of who sees what, and when.
3. Auditable Logs with Verifiable Privacy
Let’s take it a step further.
Suppose a regulator says, "Prove that every payment you made last quarter went only to verified partners and stayed within legal limits."
Apple doesn’t need to hand over every individual transaction. Instead, it can generate a Zero-Knowledge summary proof — a cryptographic receipt that proves:
- All payments went to KYC-approved entities
- All transactions followed the rules
- All required taxes or fees were applied correctly
But it does this without showing the raw data.
This is like baking a cake and showing a lab test that proves you used flour, eggs, and sugar in the right proportions — without giving away your exact recipe.
It allows full accountability, without exposing sensitive details.
4. Technical View: How Controlled Visibility Works
Technically, here’s how this might be designed:
- Every transaction is encrypted at the time it’s created
- Viewing rights (for auditors, regulators, compliance teams) are defined at the ZK circuit level
- Each viewing party is issued a view key, which gives them access to only what they’re allowed to see
- The blockchain also records who accessed what, and when, creating a secure audit log
This is not secrecy for the sake of hiding. It’s controlled, traceable privacy, designed to meet regulatory needs without compromising business confidentiality.
An Alternative Layer: Multi-Party Computation (MPC) for Shared Visibility
Now, let’s consider a slightly different approach to privacy — one that’s useful when no single party should have full visibility by default.
This is where Multi-Party Computation (MPC)comes in.
What is MPC, Simply?
MPC is a cryptographic method that allows multiple parties to collaboratively compute on encrypted data, without anyone ever seeing the full data. For example, a compliance team, a regulator, and an auditor could each hold a part of the system, and together they could validate a transaction's legitimacy, without any single party accessing the raw transaction data.
One major family of MPC protocols uses secret-sharing schemes such as Shamir’s Secret Sharing, while others rely on techniques like garbled circuits. In a secret-sharing setup, the original secret is split into “puzzle pieces” and given to different participants; no single piece reveals anything useful, but when the required subset of trusted parties collaborates, they can combine their shares and recover the full information.
MPC lets the compliance team, regulator, and auditor jointly run a validation algorithm on secret-shared transaction data so no one sees the plaintext during routine checks. The symmetric decryption key is itself split with Shamir’s Secret Sharing; only a quorum (minimum required party), say, any two of the three, can later reconstruct the key and reveal the raw transaction when law or policy demands.
In a stablecoin workflow, you can keep day-to-day privacy yet still allow full disclosure when a quorum agrees:
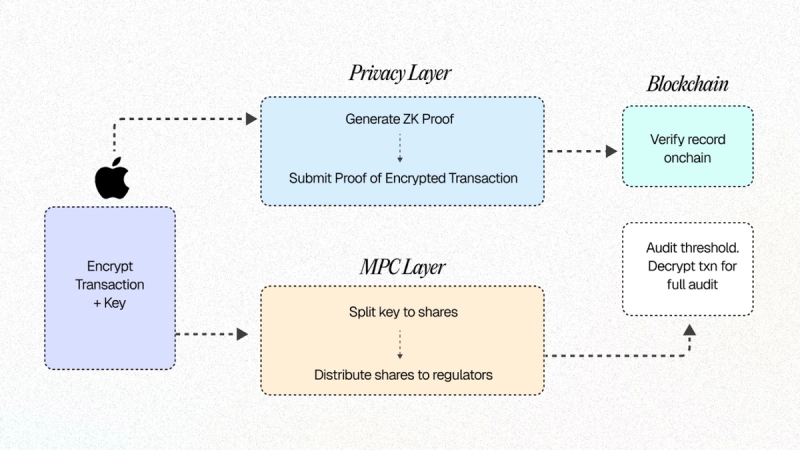
- Encrypt once. Each transaction is sealed with a symmetric key K.
- Split the key, not the data. Using a t-of-n secret-sharing scheme,K is divided into shares and distributed to the compliance desk, a regulator, and an external auditor.
- Run validation privately. The stakeholders run an MPC protocol on the encrypted payload, so they can confirm legality and risk metrics without ever seeing the plaintext.
- Permit controlled disclosure.If a legally authorised review is needed, any t of the parties can combine their shares, reconstruct K, and decrypt the transaction for a full audit trail.
Real-World Example
Let’s say Apple is making cross-border payments and needs to comply with both US and EU financial oversight.
They generate a ZKP to protect the transaction data, and then:
- Break the view key into 3 pieces
- Give one to their internal compliance team
- One to the US regulator
- One to the EU regulator
Unless at least two out of the three agree, the sensitive data remains locked.
This ensures:
- Shared governance
- No single party can spy on the data
- Every access is intentional and accountable
Why This Matters
MPC solves a slightly different problem than ZKPs. It’s not just about hiding data — it’s about collaboratively managing access in high-trust, multi-party environments.
This is useful when:
- Regulations require oversight by multiple authorities
- Corporations want a separation of powers internally
- You want to build auditability without centralization
ZKP and MPC: Better Together
These two technologies aren’t in competition. In fact, they can be layered together.
- ZKPs keep transactions private and provable
- MPC ensures that access to that data is shared, secure, and governed by consensus
Together, they offer the ideal foundation for privacy in stablecoin infrastructure.
ZKP Flow: View keys built-in
ZKP + MPC Flow: Keys split and distributed, access granted upon consensus
Closing Thought: Building for the Boardroom
Today’s blockchain systems often assume that transparency equals safety. But for a large enterprise, that idea falls apart the moment competitors or even vendors can trace, analyze, or reverse-engineer financial activity onchain.
Zero-Knowledge Proofs and Multi-Party Computation offer a better path — one where privacy and compliance don’t have to conflict. We can design infrastructure that draws a clear line between legitimate oversight and unnecessary exposure.
Regulators still get clarity. Enterprises still retain control. And stablecoins evolve from being just a wallet feature to becoming a secure foundation for global business.
This is what it takes to bring stablecoins into the boardroom.
About Blockradar
Blockradar provides secure, developer-friendly stablecoin infrastructure for fintechs. Our non-custodial wallet APIs, transaction monitoring, and AML compliance tools make it easy to launch and scale stablecoin-powered financial services. From USDC and USDT payouts to onchain expense management, we help companies move money instantly and safely across borders—without building blockchain infrastructure in-house.
Blockradar is trusted by payment platforms, remittance providers, and Web3 startups building the future of finance.
Explore our API documentation and get started at https://blockradar.co

